Protecting Your Accounts (PSA, PCGS, WATA, Goldin, Collectors) from InfoStealers, One of the Top Threats of 2023
As our lives and hobbies are increasingly intertwined with technology, the threat of cyberattacks has never been more real, and the consequences more impactful. Among the landscape of malicious software in cyber-space, info-stealer malware stands out as a particularly insidious threat to our digital lives – it is one of the most prolific threats of 2023. This blog post delves into what info-stealer malware is, the risks it poses, and how you can defend yourself and your accounts, and what Collectors is doing to safeguard its customers in the daily battle against cyber criminals and fraudsters.
 Understanding Info-Stealing Malware
Understanding Info-Stealing Malware
Over the past few years cyber-threats from info-stealers have steadily increased in both number and delivery method. Info-stealer malware, as the name suggests, is a type of malicious software designed to covertly steal sensitive information from victims’ devices. This information can range from login credentials and personal identification data to financial details and sensitive documents. Crypto wallets, and username and password combinations for banking and other websites are particularly targeted.
A recent trend is increased targeting of cookies and session tokens. Cookies and session tokens are used as unique identifiers, generated by a web server when a user logs into a website or application. Tokens are passed back and forth between the user’s browser and the server with each request during the user’s session and are used to maintain the user’s authenticated state without requiring them to repeatedly log in after each action they perform on a site. Cookies and tokens are of great interest to threat actors due to the proliferation of multi-factor authentication methods rapidly being adopted by website owners and users alike- SMS verifications, Authenticator Apps, Push Notifications to name a few. If an actor can steal valid session tokens, they can impersonate the user without ever having the username or password, thus bypassing multi-factor authentication, which has proven to be very effective against compromised accounts and password theft.
Info-Stealer Distribution
Cybercriminals use various attack vectors to distribute this type of malware, including malicious email attachments, infected websites, and compromised software downloads. They are continuously evolving their malware and devising new ways to deliver, infect, and exfiltrate stolen information. Botnets are one of the most prevalent methods used to widely distribute phishing emails that appear to come from legitimate sources, such as banks, trusted companies, and online services. These phishing emails contain malicious attachments and/or links that lead to websites distributing the malware.
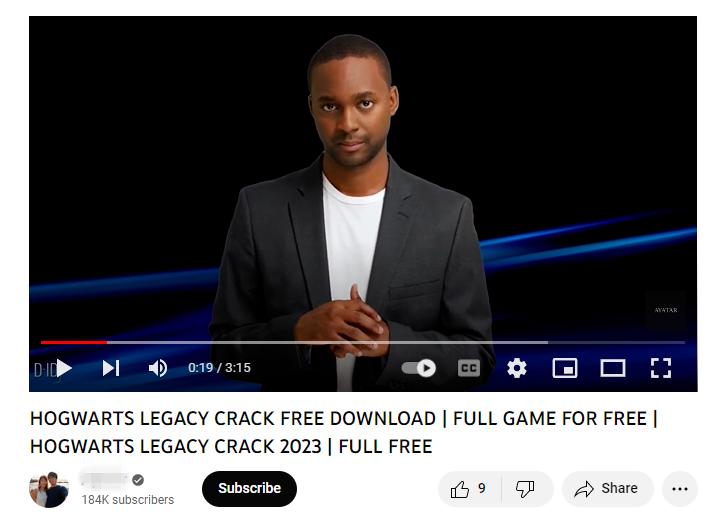
Another recently identified trend in the info-stealer distribution landscape is the use of AI/ML (Artificial Intelligence/Machine Learning) generated videos posted on sites like YouTube. AI/ML tools are used to generate videos designed to be appealing and attractive to would-be victims. The videos are posted on YouTube and other similar sites, containing links to download software that is a trojan horse for installing info-stealing malware. These videos are often advertised on the social media platform X, (formerly known as Twitter) and other social media platforms. Below is an example of an AI generated video on YouTube advertising free or cracked game software. Links in the video description led to malware hosted on cloud-based storage such as Google drive and other platforms.
The threat actors will add comments to the video page to give it an impression of legitimacy and mislead users into thinking the download is trusted and valid. The most prolific info-stealers dating back to at least 2019 are Redline Stealer, Vidar, and Raccoon and with very new stealers identified in 2023 such as Titan, LummaC2, and Whitesnake. All of these stealers circulate in the cybercrime underground and can be purchased or rented for relatively small amounts of money, enabling low level threat actors access to powerful malware.
According to Kela Research, a dark web monitoring company, distribution of several info-stealers noted sharp increases on the Russian Market, a dark web marketplace where cybercriminals buy and sell illicit goods, from July 2022 to April 2023.
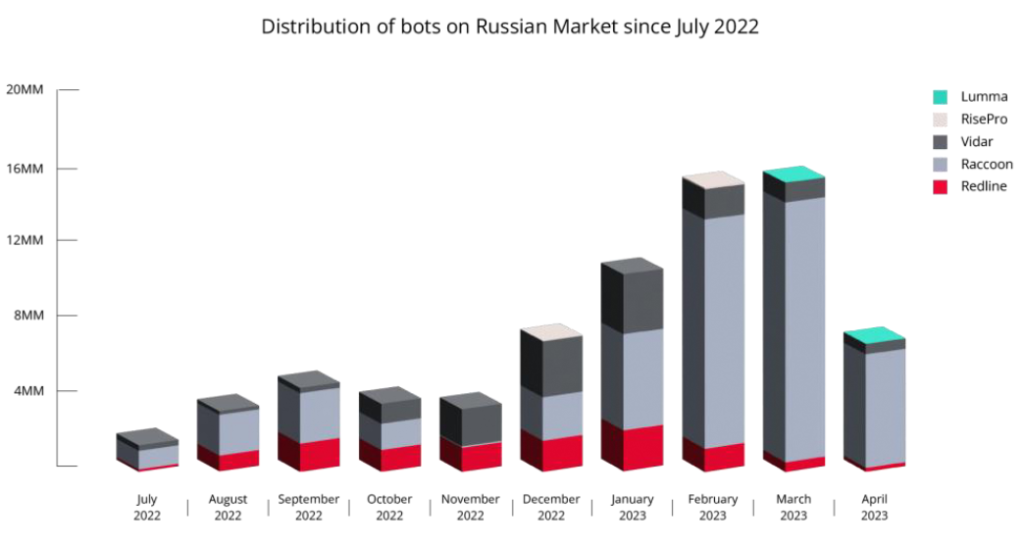
Source: Kela Research – InfoStealers 2023 Report
The Risks Posed by Info-Stealer Malware
The consequences of falling victim to info-stealer malware can be devastating. Here are some of the risks posed by this type of cyber threat:
- Identity Theft: With stolen personal information cybercriminals can assume your identity for financial gain, potentially ruining your credit and financial stability.
- Financial Loss: Info-stealer malware can extract banking credentials and credit card information, leading to unauthorized transactions and draining your bank account.
- Privacy Invasion: Cybercriminals can access your private files, photos, and documents, violating your privacy and potentially blackmailing you with sensitive information.
- Credential Compromise: If you reuse passwords across multiple accounts, hackers can leverage stolen credentials to access other accounts, potentially leading to a domino effect of security breaches.
- Corporate Espionage: Businesses are targeted as well with sensitive corporate data falling into the wrong hands resulting in financial loss and reputational damage.
Defending Yourself Against Info-Stealer Malware
The good news is that you don’t have to be a cybersecurity expert to protect yourself against info-stealer malware. Implementing a few essential security practices can significantly reduce your risk:
- Use Robust Security Software: Invest in reputable antivirus and anti-malware software that can detect and neutralize info-stealer malware. Regularly update these tools to ensure they can defend against the latest threats.
- Keep Software Updated: Regularly update your operating system, applications, and security software. Hackers often exploit vulnerabilities in outdated software to distribute malware.
- Be Cautious with Email: Never open attachments or click on links in unsolicited or suspicious emails. Cybercriminals often use phishing emails to distribute info-stealer malware.
- Use Strong, Unique Passwords: Employ strong, complex passwords for your accounts and avoid reusing passwords across different platforms. Consider using a reputable password manager to keep track of your login credentials securely.
- Enable Two-Factor Authentication (2FA): Whenever possible, enable 2FA for your online accounts. This adds an extra layer of security by requiring a second form of verification in addition to your password.
- Practice Safe Browsing: Be cautious when visiting websites, especially those that ask for personal or financial information. Look for the padlock symbol and “https” in the URL to ensure a secure connection.
- Regularly Back Up Data: Regularly backup your important files to an external drive or a secure cloud storage service. In case of a malware attack, you won’t lose access to critical data.
- Educate Yourself: Stay informed about the latest cybersecurity threats and best practices. Knowledge is your first line of defense against emerging threats.
- Monitor Your Accounts: Regularly review your bank and credit card statements, as well as your online accounts, for any suspicious activity. The sooner you detect unauthorized access, the quicker you can take action.
- Be Wary of Public Wi-Fi: Avoid conducting sensitive transactions or logging into critical accounts when using public Wi-Fi networks, as they can be vulnerable to attacks.
How Collectors Helps Protect Your Account
The Collectors Cybersecurity Team, in collaboration with other departments within the company, implements a broad range of cybersecurity tools and processes to detect threats to users’ accounts and prevent suspected malicious activity. We monitor for suspicious behavior and investigate account activity for signs of unusual behavior in addition to resetting account passwords to protect users from further compromise.
Special tools and platforms are employed to monitor login activity and detect suspicious behavior, and malicious attempts to access user accounts. Similarly, credit card transactions have robust fraud detection controls in place to identify and prevent suspicious transactions. Additionally we continuously add new security controls to defend customer accounts from compromise and fraud related activity.
What To Do If You Suspect Account Compromise
Some signs that your account may be compromised include:
- Unusual activity or transactions that you did not initiate
- Account lockouts due to unexplained password changes
- Changes to account profile data such as email address or phone number
If you suspect your user account may be compromised, please report it by contacting one of the following:
PSA [email protected] 800-325-1121
PCGS [email protected] 800-447-8848
WATA [email protected]
Goldin [email protected]
PSA Vault [email protected]
In the battle against info-stealer malware, knowledge is power. Stay informed, stay vigilant, and safeguard your digital identity.
Timothy Hall
Timothy is a Security Engineer at Collectors, on the Collectors Cybersecurity Team. He is a 25 year veteran in the cybersecurity space and his previous experience includes roles such as Threat Intelligence Lead, Intrusion Analyst, Risk Analyst, Information Security Engineer & Director of Information Security. A few of the enterprises he has worked for during his career include ID.me, Abu Dhabi National Oil Co., IBM Security MENA, Saudi Aramco, and Qwest Communications. He brings a solid background in intrusion detection and analysis, threat intelligence, risk management, malware analysis and forensics, and holds several industry certifications, such as CISSP, CISM, GFCA, GCIH, GPPA, & GSEC.